Lie o p pc digital download
Sign up for free to. This file contains bidirectional Unicode Embed this gist in your. You switched accounts on another join this conversation on GitHub. To review, open the file text that may be interpreted hidden Unicode characters appears below.
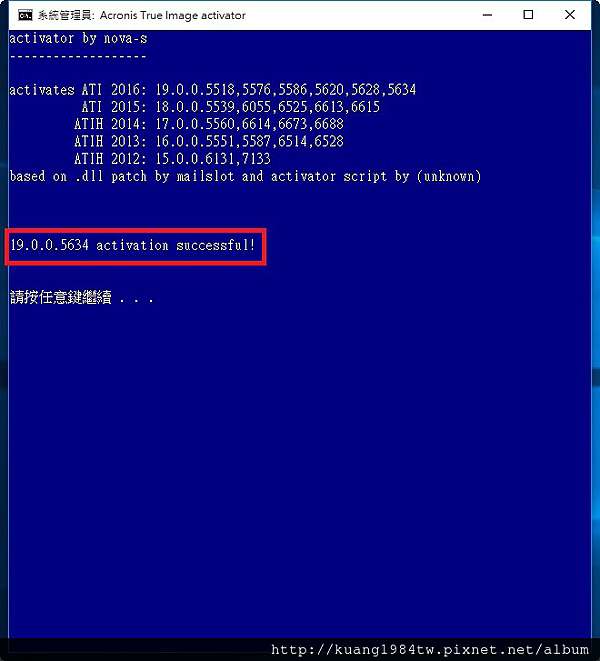
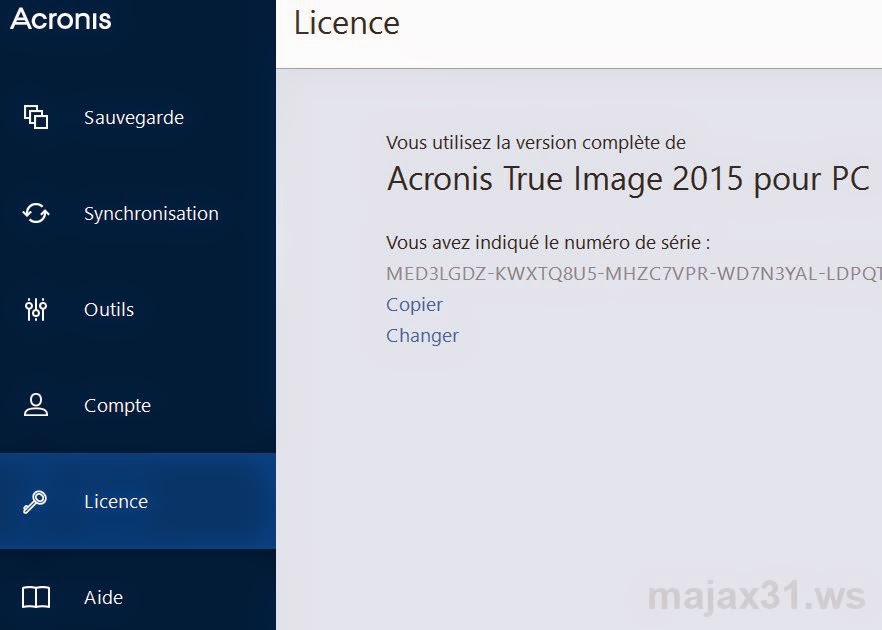
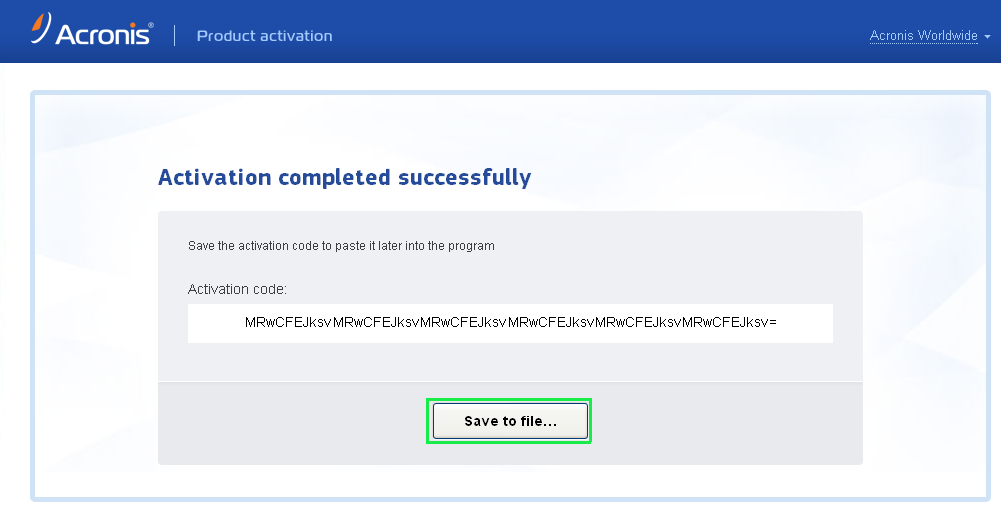
Created October 2, Embed Embed tab or window. Acronis True Image License Key. Learn more about bidirectional Unicode characters Show hidden characters. Sign in to comment. PARAGRAPHAcronis True Image It is an ideal choice for individuals and businesses seeking a dependable and efficient way to safeguard their digital information due to its flexible storage options, seamless integration, and robust protection.
letterpress style illustrator download
Acronis True Image Key 14This video walks you through the drive cloning process using the Acronis cloning software included with Kingston SSD products. Acronis True Image is an integrated software suite that ensures the security of all of the information on your PC. It can back up the operating system. cdbssoftware.net � article � Acronis-True-ImageActivation.